Writings & Media
2026
Webinars
Blogs
-
Reflecting on AI in 2025: Faster Attacks, Same Old Tradecraft
-
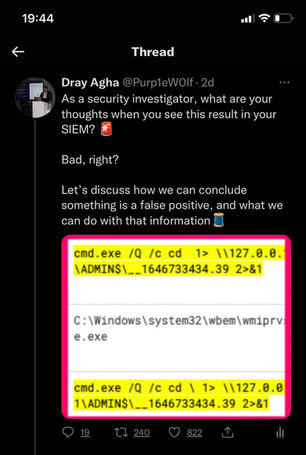
EDR Killer Case
-
Media commentary [1]
-
Media comments
-
Comment on ChatGPT 'Health' security implications [1]
-
Comment on Manage My Health compromise [1]
-
Comment on London council cyber attacks [1]
2025
Webinars
-
Research on common initial access
-
Routine adversary tradecraft
-
CentreStack Vulnerability & the Future of the CVE
-
Creating a Hostile Environment for Threat Actors
-
How the Hunt Happens: Q&A With the Huntress SOC
-
EDR + SIEM for Faster, Smarter Threat Response
Blogs
-
Untold Tales from Tactical Response
-
Initial access brokers exposed
-
Utilising ASNs for Hunt & Response
-
Ransomware Playbook Analysis
-
SIEM foundations
-
Hypervisor Defences
Sonicwall SSLVPN Compromise August 2025
Fortigate SSO Compromise December 2025
-
Warned community of exploitation [1]
Media comments
-
Comment on Jaguar Land Rover cyber attack [1, 2]
-
Comment on British industry fragility to cyber attacks [1]
-
Extended Interview on backup posture [1]
-
Comment on Spring 2025 series of UK Retailers compromised [1, 2, 3, 4]
-
Protecting UK engineering manufacturing from compromise [1]
-
Comment on ClickFix malware [1]
-
Comment on critical national infrastructure cyber security [1]
-
Comment on securing edge devices [1]
-
Comment on the security risks from the TikTok/Rednote transfers [1, 2]
-
Comment on Apple Encryption downgrade as requested by UK Gov [1, 2]
-
Comment on security for critical national infrastructure [1]
-
Preventing Ransomware [1]
-
Comment on password resiliency [1]
-
Comment on Kellogg compromise via Cleo file transfer exploit [1]
-
Comment on European CVE alternative [1]
-
Comment on rumoured Cisco compromise [1]
-
Comment on phishing for Forbes [1]
-
Comment on Infostealers [1, 2]
-
Comment on S3 bucket compromise [1]
-
Comment on efficacy of emoji-based credentials [1]
-
Comment on new Ofcom rules for child internet safety [1]
-
Comment on NCSC updated cyber security guidance [1]
-
Comment on Zacks investment compromise [1]
2024
Webinars
Cleo CVE-2024-55956
ScreenConnect `Slash & Grab` CVE-2024-1709 & CVE-2024-1708
Fortigate's CVE-2023-48788
Most Threat Actors Aren't Sophisticated
Twitter Threads
I like using Twitter threads to share real attack data, or defensive and investigative techniques
2023
Webinars:
Conferences:
Podcasts:
Featured on Richard Tubb's tech podcast October 2023
And again on Rich Tubb's podcast December 2023
MOVEit Transfer 0day
One of the Huntress investigators for the MOVEit Transfer 0day, we also were amongst the first in the community to begin sharing details and response guidance
M365 and Azure investigations
A number of blogs on our investigations in m365/Azure world
Blog one on investigation into a series of compromises across multiple networks
Blog two on leveraging anomalous user-agents in M365 telemetry to conduct threat hunts
Addressing Initial Access
Short blog with Harlan Carvey on how to engineer defence-in-depth against common initial access techniques involving OneNote malware, macro malware, and ISO mounting
You can find the article here
The Methods Behind a Huntress Managed Antivirus Investigation
Following how a Defender alert instigates an investigation involving Event Logs, and ending with tips on how to communicate findings in a report
You can find the article here
Registry Collection Script
Made with Harlan Carvey and John Hammond, a simple PowerShell script to automate collection of important Registry hives, Amcache, and each user's NTUSER and UsrClass .dats
You can find the script here
Media Comments
Comments on NCSC's latest Cyber Action Plan tooling
Comment on the March 2023 release of the US National Cybersecurity Strategy
Comments on 'Citrixbleed'
Twitter Threads
I like using Twitter threads to share real attack data, or defensive and investigative techniques
Suspicious M365 User agent hunt [1]
Lateral movement [1]
Persistent obfuscation [1]
Catching failed evasion [1]
Sysmon for rapid malware analysis [1]
Summarising Remote Desktop Gateway intrusion investigation [1]
Jumplist forensics to solve problems [1]
Pulling scheduled task data out of the Registry [1]
Qakbot tracking [1]
Leveraging alternate logs when threat actors wipe the standard security event logs [1, 2]
Detections based on execution from anomalous directories [1]
2022
Webinars:
Quick Forensics for the Lazy Investigator. Supporting Github repo
Rapid Malware Analysis. Supporting Github repo
Cleartext Shenanigans: Gifting User Passwords to Adversaries With NPPSPY
Article on a novel, malicious credential technique that was previously thought to only be theoretical. We encountered this in the wild whilst investigating a ransomware intrusion.
You can read the article here
This article had some wonderful interaction on Twitter [1, 2, 3, 4], as well as some discussion on Youtube [5]
Defense Evasion series
Three-part series on what defense evasion is and how to architect foundational security to catch adversarial techniques
Evicting the Adversary
How to kick out an active attacker is a gap I've noticed in many blue team guides that advise monitoring and detections. This article addresses that with granular guidance on ejecting an attacker
You can read the article here
This article generated some interaction on Twitter [1, 2], and made it onto a podcast or two [3]
This article made it into Ollie Whitehouse's security news
Accidental detection ProxyNotShell variant
When sharing data from a recent intrusion we had worked, CrowdStrike researchers took a puzzle piece we had and identified we had in fact found a new variant exploit for CVE-2022-41080 and CVE-2022-41082 [1, 2, 3]
This was circulated in the security community
And mentioned in some notable security spaces
Media Comments
Comments on the current industry problems with entry-level hiring [1, 2]
On the MS-MSDT zero-day CVE-2022-30190
On the Confluence RCE in Summer 2022 CVE-2022-26134
On supply chain findings from Verizon's DBIR report
Perspective on supposed increase in ScreenConnect's usage by threat actors.
Brief comments on the preferred initial access MedusaLocker (ransomware actor)
Brief comments on EU 'smart device' security proposals
Brief comments on ProxyNotShell mitigation confusion
Contributions to WTFbins
Encyclopedia of false positive activities that Defenders may encounter
Executable called Bloodhound, but not connected to AD Mapping tool
Twitter Threads
Answering Chris Sanders' thoughts on how to investigate a mounted ISO alert [1]
Hunting adversaries who use the same directories [1]
Thoughts on detecting Winexesvc [1]
Overcoming security silos make your investigations better [1]
Security solutions and starting your intrusion investigation [1]
Defeating Suborner [1]
Leveraging the forensic data from security solutions [1 , 2]
Investigating false positives and circulating your findings to the infosec community [1, 2]
Leveraging Velociraptor, Kape, Sigma, Chainsaw, and Security Onion to rapidly detect evil in Windows Event Logs [1 , 2]
Reverse engineering and monitoring an AMSI & ETW bypass [1, 2]
Sysmon streamliner
Script to spin up Sysmon with Florian Roth's ruleset, and then deploy Ippsec's Sysmon grepper that extracts IoCs
You can find the script here
2021
No Logs? No Problem! Incident Response without Windows Event Logs
In this article I share a number of easy-to-deploy digital forensics techniques I've found helpful during an investigation, when the logs have been burned
You can read the article here
This article generated some interaction on Twitter [1, 2, 3]
I was also grateful to appear once again in Ollie Whitehouse's security news
PowerShell Jobs
This article was inspired by an adversaries' malicious PowerShell technique I found during an incident response.
You can read more here
This article made it into Ollie Whitehouse's security news
The Science Behind Cyber Security
A scientific lens to the philosophy, practices, and solutions in the infosec world
Comment for IoT Vulnerabilities
The Daily Swig kindly requested I offer some perspective on some significant Realtek vulnerabilities that affected a load of IoT devices.
If you scroll to the bottom of the article, you'll find some of my comments here
Windows’ Registry Run Keys
Here I wrote about an obscure feature of the Windows registry that could gift an adversary sneaky persistence.
You can read more here
Follow up in early 2022 with more data
The article was referenced as 'editor's pick' in the Blue Team News and in Ollie Whitehouse's security news
I was also grateful that this article gained traction on Twitter [1, 2, 3]
HiveNightmare
Honestly the infosec community and their names. I wrote about the permissions error in critical Windows files that would allow an adversary to escalate privileges and steal credentials
Created a script and GitHub repo that simplified the confusion of which machines were vulnerable and how. You can read more here
Our method was referenced in one or two articles also.
There were great responses from Twitter on this one [1, 2 ,3]
PrintNightmare
I wrote two things about the PrintNightmare Windows exploit.
I created a step-by-step guide to check if post-patch machines were still vulnerable and could still be exploited
I wrote a network analysis research piece on what the PrintNightmare looked like from a network perspective. Please click here for a copy with fewer distracting colours
This received some awesome Twitter interaction [1, 2, 3]
Active Directory Certificate Services
SpectreOps wrote a brutal offensive security research piece all about exploiting Microsoft's implementation of Public Key Infrastructure in their Active Directory, called Certificate Services. I extrapolated the defensive guidance in their report, expanded on it, and found alternative hardening techniques.
You can find an online copy here.
There was great Twitter interaction for this defensive guidance [1]
Microsoft Exchange 'ProxyLogon' Zero-Day
I was the incident responder for Exchange in idents during this time. I also identified a number of mistakes some sysadmins had made when patching their Exchange servers.
I collected the mistakes and their fixes together and bundled it into a quick guidance piece we released to the public.
The Blue Team Notes
I open sourced the Blue Team Notes, dedicated to digital forensics, incident response, threat hunting, malware analysis, and more!
2020
Police Digital Security Centre
In conjunction with the PDSC, I released a small series of cyber security guidance. It was written for non-technical small businesses.
Masscan to Nmap
I duck-taped together two network scanners with Python. This was to leverage the advantages of both as simply as possible
Read more on the Github page
Hack the Box Writeups
I began to publish walkthroughs of lab machines from Hack the Box!
2019
Psychology and Cyber security
Short article on the benefits of interdisciplinary insight from psychology in cyber security. Published in the The British Psychological Society's PsychTalk
Extract can be found here
Cyber War, Supply Chains, and Realism in Lithuania
A NATO-supported trip to Lithuania resulted in a short blog post all about the cyber security threats and proactive defences that the Lithuanian state takes
Find a digitalised copy here
You can find a scary video of me, talking in Lithuania about cyber security, military practice, and international cooperation.
Video here, I pop up between 1:58-2:17
Cyber Security for Small Businesses: A Review Of the Advice
SME's employ half the UK's working adults. Yet security advice and products strangely ignore them. For an NCSC event, I wrote up why this is the case and what good advice exists anyway.
Click here for a copy of the poster
Cyber Espionage Conference & Report
A collaborative event between Oxford and Royal Holloway. I co-edited the report, as well as spoke at the event on the philosophies and doctrines fuelling Russian cyber antagonism
Click here for a PDF of the report
The English Language in Computer Programming
I gave a short talk in Washington, DC, about the politics of the English language in many computer programming languages
A few details can be found here